Who’s behind Exodus iOS and Android spyware?
Exodus is the spyware making the headlines these days. It is designed to run on iOS and Android and has been discovered during a security research made at Security Without Borders and firstly published on Motherboard. Since then, it has appeared on many other tech websites, such as TechCrunch, Wired and The Hacker News.
To work on Android it performed three stages, with the final one using the Dirty COW exploit (CVE 2016 5195) to obtain root privileges and run persistently on the user’s device. iOS apps are sandboxed by design and Apple controls app published on the App Store, so life’s harder for the iOS version. To infect users this variant abuses of Apple Developer Enterprise program, something that seems too easy to obtain. Others have been doing the same. Facebook and Google recently appeared on the list as well, even if for purposes other than spreading illicit apps. If you’re interested on deeper technical details, the iOS variant has been discussed at Kaspersky Security Analyst Summit by Lookout, who wrote about, too.
But it’s the story behind this spyware is what’s more interesting.
As written by security researcher Claudio Guarnieri on his blog, the software seems to have been designed for Italian law enforcement to use. Weirdly enough, it has been found in as many as 25 Android apps, which were publicly available (now removed by Google) on the Google Play Store. Those apps may have been downloaded by anyone with and Android smartphone and some were even disguised as mobile telco assistance ones. Motherboard reports the impacted users are less than 1000 and all in Italy. The people developing it, through different companies (CONNEXXA and eSurv), have used to have contracts with prosecutor’s officies all over Italy for long time. But during an apparent glitch of the network behind the spyware, the prosecutor’s office of Benevento discovered spied data wasn’t stored on a local server (as required by the Italian law) but sent to AWS instead. Surprisingly enough, the local server was empty, with no OS installed at all. There could have been many reasons for this, yet I can’t find a good one. If going local wasn’t a option for them, there are cloud companies in Italy, like Aruba and Netsons, which provide storage and processing power inside the borders and in compliance with the Italian law. Some say they spied people on behalf of third-part unknown authorities, maybe criminal organizations, although that’s unconfirmed. On April 1, 2019 the prosecutor’s office in Naples has communicated it started investigating on the matter (PDF).
Hard to deny, all of the above made me curious about the people behind this. So I got back to the keyboard. Here is what I’ve found.
The company behind
Disclaimer: data and findings shown below are public on the Internet and have been gathered using publicly available tools. Therefore this post is just a collection of that data and no break has been performed to obtain it. Furthermore, while some of the tools hereby shown are commonly used to perform malicious actions, this post does not encourage doing so.
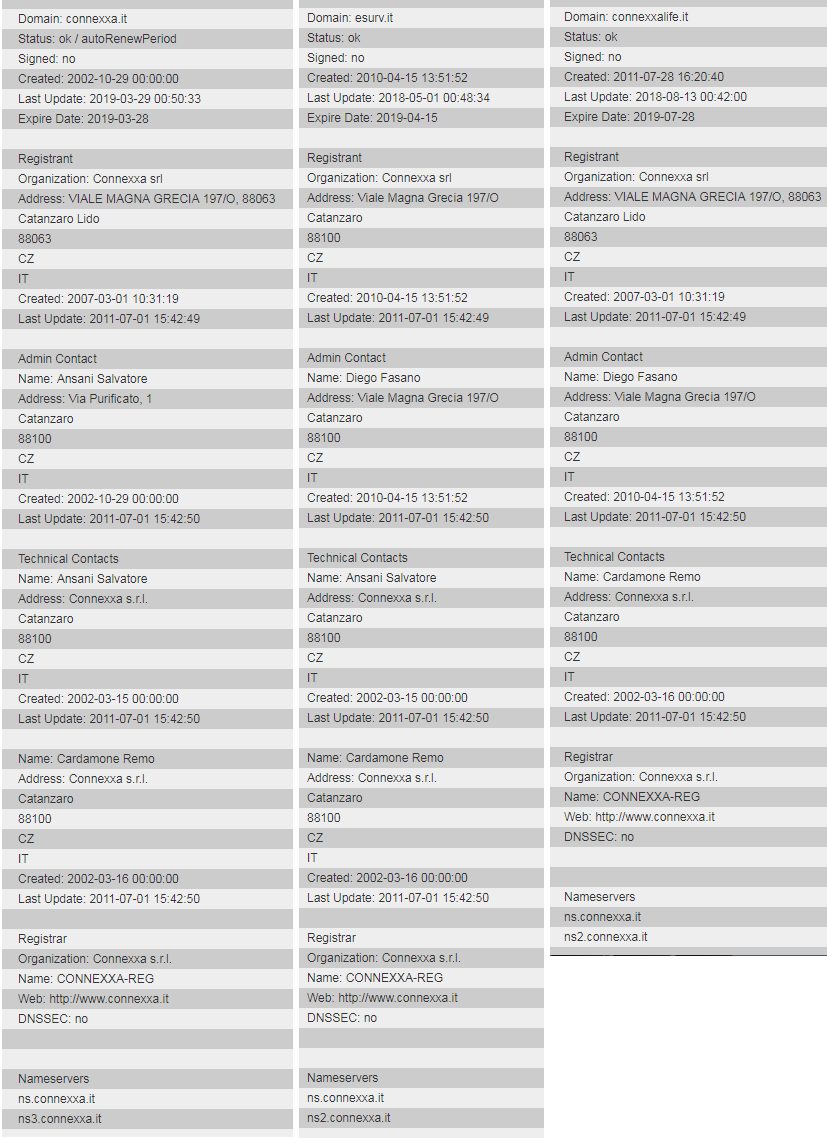
CONNEXXA is the name of the company who developed the spyware. The name has been found in provisioning profiles and distribution certificates inside IPA app packages deployed via the Apple Enterprise Certificate program. eSurv and Connexxalife popped out from my Google searches. The company was kind of split in two. The first one is responsible of developing surveillance software and the second one provides IT solutions to hospitals and medical centers. Their websites are easily discoverable and even if some have been taken down (replying an HTTP 200 and an empty body), content is still readable from Google cache. Unfortunately no saved history is present on archive.org.
They may have foreseen a security scandal and hoping to keep their second business away from it, in January renamed Connexxalife to Nufirst and moved the legal address from Catanzaro to Cologno Monzese (Province of Milan). They kept the same VAT number (as required by the law) and partnerships, one of which with the Italian Ministry of Education, University and Research (link).
| Company name | VAT # | Founded | Website | website up? |
|---|---|---|---|---|
| CONNEXXA S.R.L. | 02537760791 | Nov 18, 2002 | www.connexxa.it | down |
| eSurv S.R.L. | 03395880796 | Nov 12, 2014 | esurv.it | down |
| CONNEXXALIFE S.R.L. (now NUFIRST S.R.L.) | 03201030792 | Oct 13, 2011 | connexxalife.it | up |
To know about their renvue and more legal details, click the VAT number. Some of the data is provided by www.agenziaentrate.gov.it.
It makes sense to whois those domains.
Wow, so plain simple. We’ve just found domains are registered to the same address and we got the names of head staff plus a confirmation that key people are the same across all of three companies. They are:
- Diego Fasano, who is CEO of the three of them
- Ansani Salvatore
- Cardamone Remo
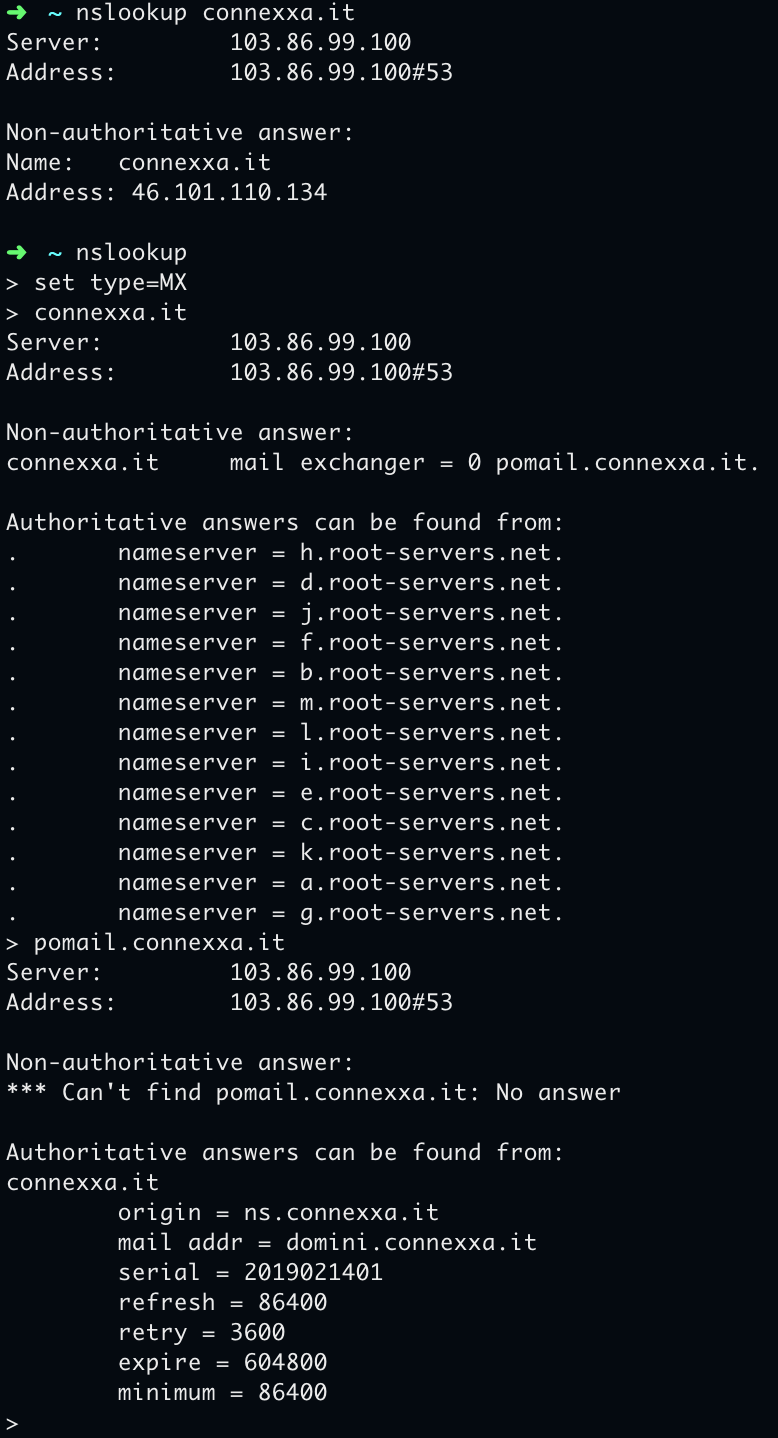
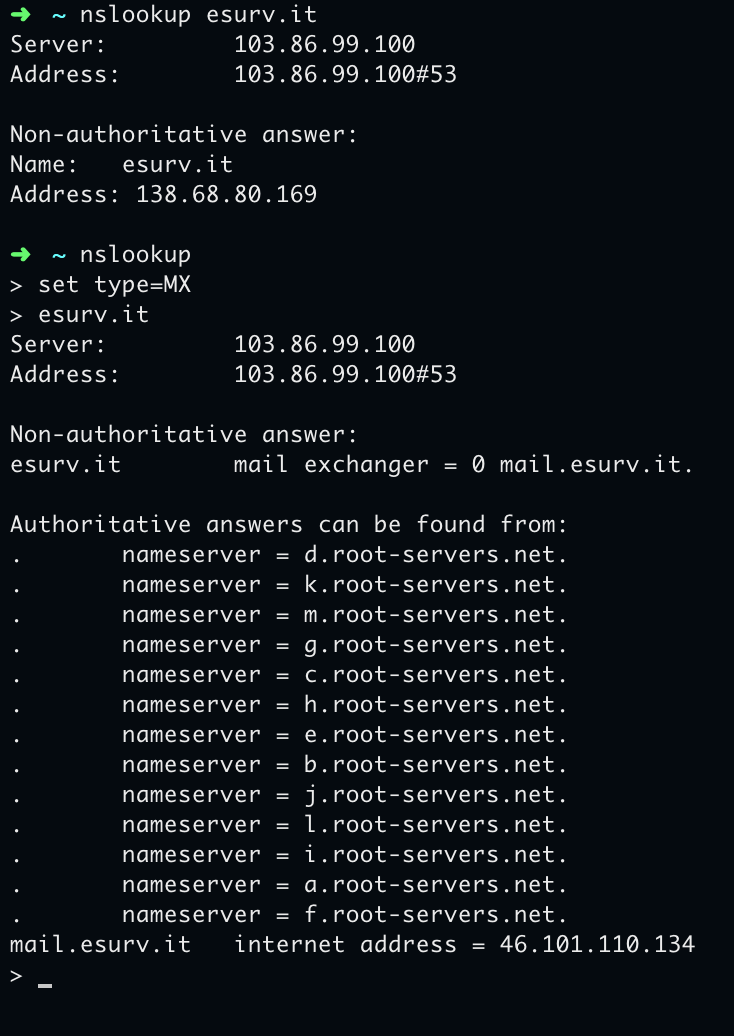
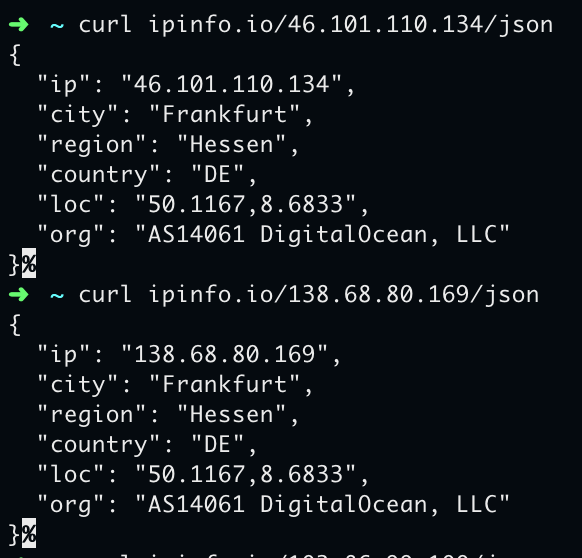
Then we ask nslookup what those domains point to. Websites run on two VPS on Digital Ocean at the Frankfurt (Germany) datacenter, one hosting connexxa.it and one esurv.it (connexxalife.it is hosted on AWS). Then we ask about MX DNS records. nslookup replies the first VPS hosts an emails server for both domains, pomail.connexxa.it and mail.esurv.it. So same people, same server, same infra.
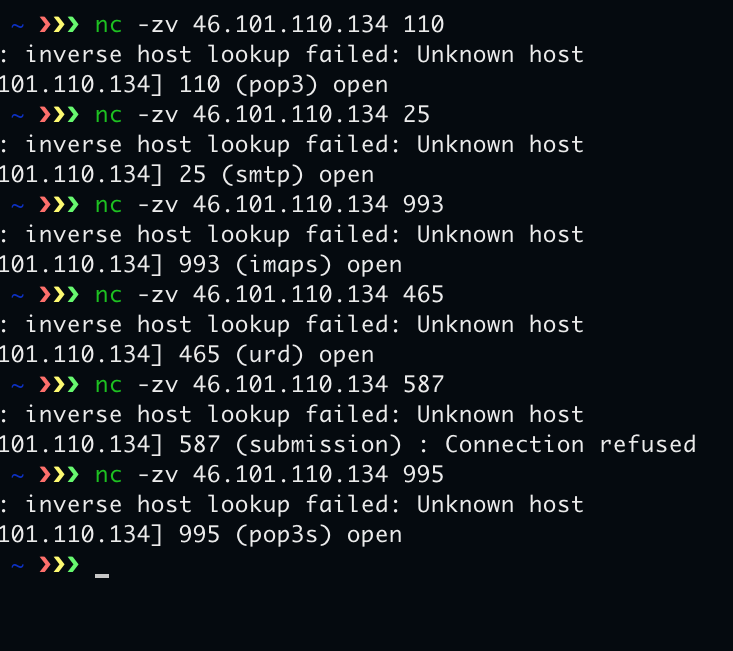
Next we knock via netcat and find they have open ports for POP3 and SMTP and use unsecure email protocols.
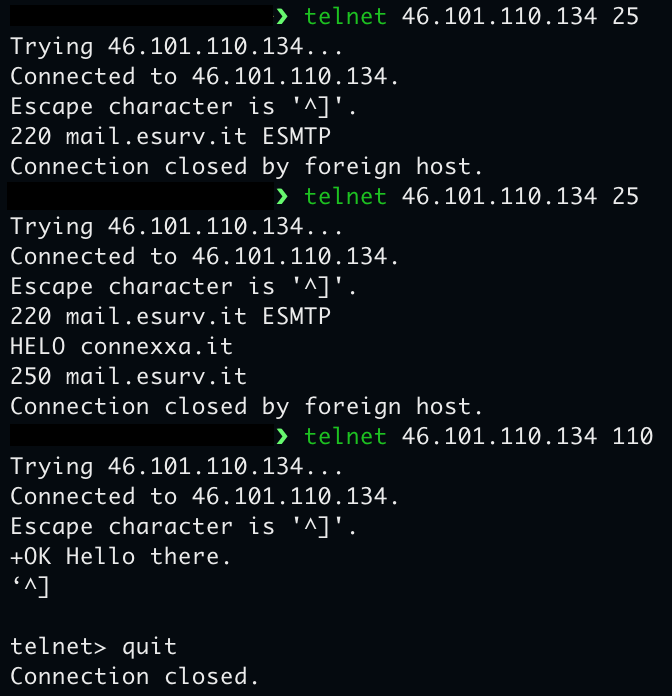
You could even telnet to them.
I guess is not that hard to find email addresses of CEO and his staff and combine that information with this. An example? Just head over hunter.io email finder. You can easily get:
- Diego Fasano, fasano [at] esurv.it
- Ansani Salvatore, salvatore [at] esurv.it
Oh my…
Conclusions
It’s jaw dropping that a company working with the government and claiming to be a leader in IT and security solutions uses unsecure email protocols. Last but not least, it is still unclear why people at CONNEXXA made what’s been reported, if it was planned and if they did on behalf of a third part. In an interview published in 2014, the CEO told his story and talked of his hopes and efforts to create an IT company in a place as difficult as the Southern Italy is. I hope truth will come out and lights will fade away shadows on the matter.
Thanks for reading.